Access Tokens
Logflare uses access tokens for user API authentication. These access tokens must be provided with each API requests, with the exception of resources that have authentication disabled by the user.
Scopes
Access tokens can be scoped to specific functionality.
ingest- allows ingestion of events into sources.query- allows querying of Logflare Endpoints.management- allows management of resources and programmatic access to Logflare functionality.
ingest and query scopes can be scoped to specific sources and endpoints. It is recommended to use the least privileged token for the given task, especially for public ingestion.
Managing Access Tokens
Access tokens can be created under the Manage Access Tokens page.
First, click on Create access token button.
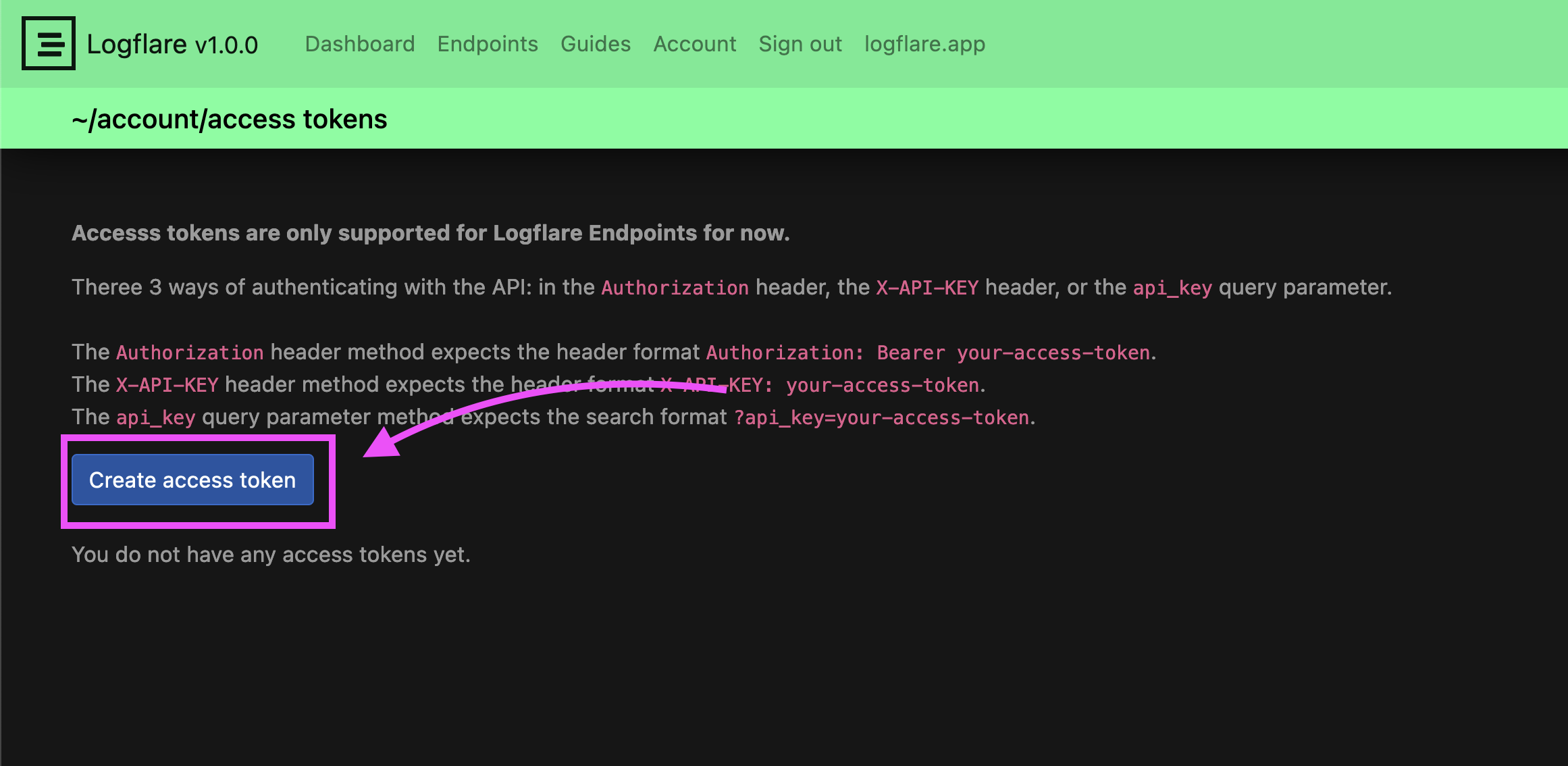
Then, enter a description for the token for reference. Click on Create once you are done.
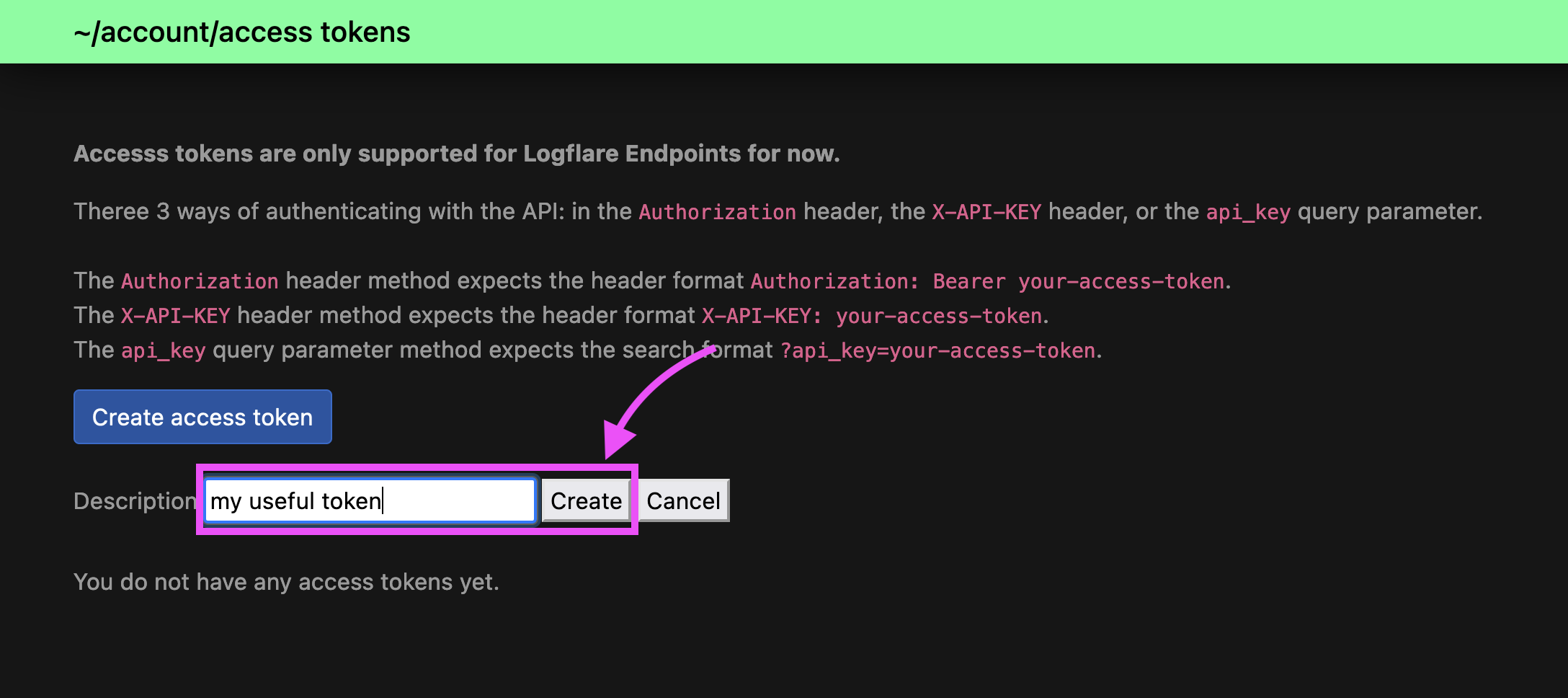
You will be shown the access token ony once. Do copy the token to a safe location.
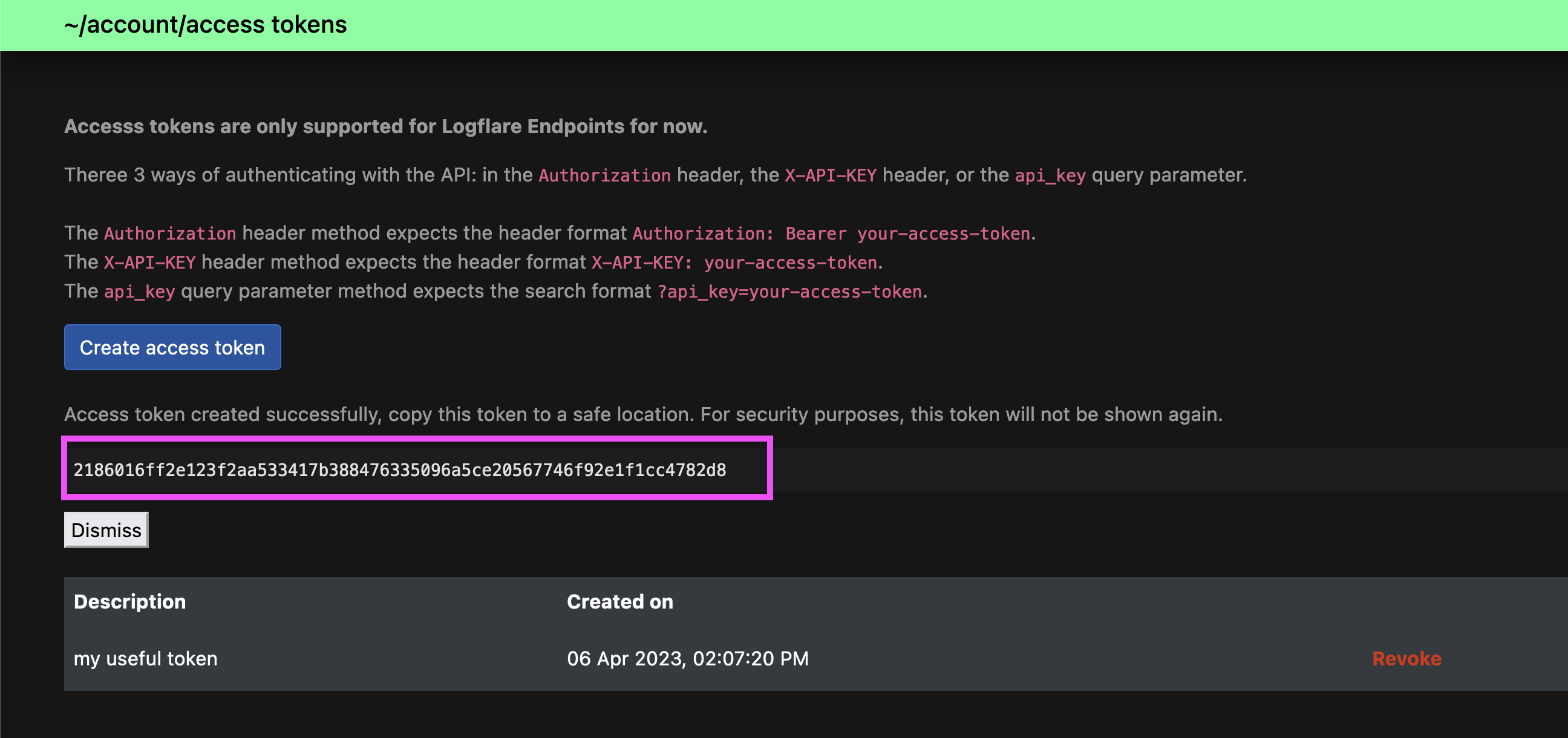
To revoke access tokens, clikc on the Revoke button. This would immediately reject all incoming API requests.
Authentication
There are 3 supported methods to attach an accees token with an API request:
- Using the
Authorizationheader, with the formatAuthorization: Bearer your-access-token-here - Using the
X-API-KEYheader, with the formatX-API-KEY: your-access-token-here - Using the
api_keyquery parameter, wuth the format?api_key=your-access-token-here
Client-side is Public
Access tokens can be exposed for client-side usage. Consider restricting tokens to ingest into specific sources or to considered public for client-side usage. Public-only tokens will not be able to access the Logflare Management API beyond the ingest/query APIs.
Private access tokens should not be exposed to the client side, as private access tokens have complete access to all management APIs used for account control.
Rotation
When rotating access tokens for client-side access tokens, we recommend creating another client-side token and performing a gradual shift to the new token before revoking the old token.
Revoking the old token while clients are still on it would result in API request errors on the client.